Definition[]
A wireless network allows computers, laptops, PDAs and other wireless devices to connect with each other and/or connect to the Internet without wires. These devices use radio waves to transmit data and messages to other wireless devices.
Overview[]
Wireless networks offer connectivity without the physical restrictions associated with building wired networks. Though generally developed as an extension to an existing wired infrastructure, a wireless network may be stand-alone as well.
Wireless networks are generally composed of two basic elements: access points and other wireless-enabled devices, such as laptops. Both of these elements rely on radio transmitters and receivers to communicate or “connect” with each other. Access points are physically wired to a conventional network, and they broadcast signals with which a wireless device can connect. The signal broadcast by the access point at regular intervals — several times per second — includes the service set identifier, as well as other information. Typically, this identifier is the name of the network. Wireless devices within range of the signal automatically receive the service set identifier, associate themselves with the wireless network, and request access to the local wired network.
Wireless networks are characterized by one of two basic topologies:
Spurred on by increasing bandwidth and decreasing costs of laptops and mobile computing, wireless networks are becoming widely available in "hotspots" in cafes, retail centers, hotels, schools, airports, and businesses.
Security issues[]
Wireless networks offer a wide range of benefits to corporations, including increased flexibility and ease of network installation. They also present significant security challenges, including protecting against attacks to wireless networks, establishing physical control over wireless-enabled devices, and preventing unauthorized deployments of wireless networks.
Wireless networks face all of the information security risks that are associated with conventional wired networks, such as worms and viruses, malicious attacks, and software vulnerabilities, but there are significant challenges that are unique to the wireless network environment. In implementing wireless networks, organizations face three overarching challenges to maintaining the confidentiality, integrity, and availability of their information:
- protecting against attacks that exploit wireless transmissions
- establishing physical control of wireless-enabled devices, and
- preventing unauthorized wireless deployments.
Protecting against wireless exploits[]
Protecting against wireless network security attacks is challenging because information is broadcast over radio waves and can be accessed more easily by attackers than can data in a conventional wired network.
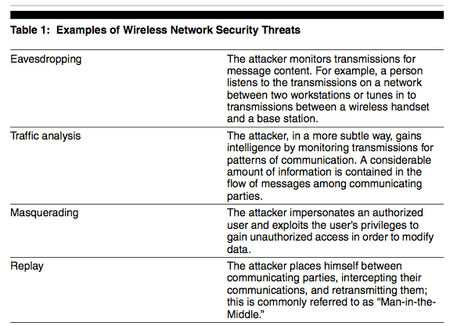
For example, wireless communications that are not appropriately secured are vulnerable to eavesdropping and other attacks. Poorly controlled wireless networks can allow sensitive data, passwords, and other information about an organization’s operations to be easily read by unauthorized users. In addition, wireless networks can experience attacks from unauthorized parties that attempt to modify information or transmissions. Table 1 provides examples of the different types of attacks that can threaten wireless networks and the information that they are transmitting.
Physical control of wireless-enabled devices[]
Physical control of wireless-enabled devices takes on new importance in maintaining information security. Areas of physical risk include the placement and configuration of wireless access points and control of the wireless-enabled device that connects to the organization's network. For example, it can be difficult to control the distance of wireless network transmissions, because wireless access points can broadcast signals from 150 feet to as far as 1,500 feet, depending on how they are configured. As a result, wireless access points can and do broadcast signals outside building perimeters. Wireless signals broadcast from within an organization's facility that extend through physical walls, windows, and beyond a building’s perimeter (signal leakage) can increase an organization's susceptibility to the various attacks described in Table 1 above.
In addition to the challenge of signal leakage, it can be difficult for wireless network administrators to track the physical location of wireless-enabled devices. For example, in conventional wired networks, users are required to physically plug in to the organization's networks via cable. This allows administrators to determine where each device is connected. However, with a wireless network, pinpointing a wireless-enabled device's location can be difficult because the device is mobile. As a result, it can be harder for information security officials to locate unauthorized devices and eliminate the risks they pose.
Preventing unauthorized wireless deployments[]
Unauthorized wireless networks create two main challenges for an organization's information security. The first challenge comes from legitimate organizations, employees, or others seeking to benefit from the flexibility of wireless networks. Because of the affordability and availability of wireless network equipment, well-meaning individuals might install unauthorized wireless-enabled devices or wireless access points into an organization's traditional wired network environment without the approval of the organization's management. As a result, an organization's information security officials might be unaware that wireless networks are being used and would therefore be unable to take the appropriate mitigating actions — such as protecting against potential wireless attacks or preventing signal leakage.
The second challenge stems from the increasing availability and integration of wireless technology into products such as laptops. For example, organizations that are not seeking to install a wireless network may find that as they purchase new equipment they are buying wireless-enabled devices. In some instances, these devices are not available without wireless technology. As a result, an organization may inadvertently procure wireless network components that could pose risks to its enterprise.
Enhancing wireless network security[]
Wireless network security can be enhanced by establishing comprehensive information security policies that address wireless security, configuring security tools to meet defined agency policy requirements, implementing comprehensive wireless monitoring programs, and training employees on wireless policies. Without effective security controls for wireless networks, information is at risk of unauthorized disclosure, modification, or destruction.
Types of wireless networks[]
The term wireless network may refer to many different types of wireless networks, including: