Definition[]
Secret key cryptography (also called symmetric cryptography)
| “ | [a] branch of cryptography in which the algorithms use the same key for both of two counterpart cryptographic operations (e.g., encryption and decryption).[1] | ” |
Overview[]
Secret key cryptography has been in use for thousands of years in a variety of forms. Modern implementations usually take the form of algorithms which are executed by computer systems in hardware, firmware or software. The majority of secret key algorithms are based on operations which can be performed very efficiently by digital computing systems.
Traditionally, this technique employs algorithms in which the key that is used to encrypt the original plaintext message can be calculated from the key that is used to decrypt the ciphertext message, and vice versa.
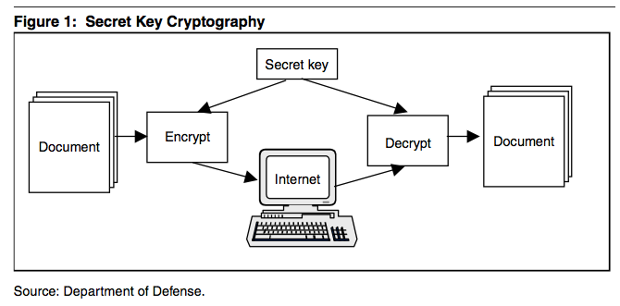
It has been used primarily to provide confidentiality. In secret key cryptography (also called symmetric key cryptography), one key is used to perform both the encryption and decryption functions. (See figure 1.) The encrypted message can be freely sent from one location to another through an insecure medium, such as the Internet or a telephone link. As the name implies, secret key cryptography relies on both parties keeping the key secret. If this key is compromised, the security offered by the encryption process is eliminated.
Common symmetric key algorithms include Triple Digital Encryption Standard (3DES) and the Advanced Encryption Standard (AES).
Secret key cryptography has significant limitations that can make it impractical as a stand-alone solution for securing electronic transactions, especially among large communities of users that may have no pre-established relationships. The most significant limitation is that some means must be devised to securely distribute and key management manage the keys that are at the heart of the system. Such a means is commonly referred to as "key management."
When many transacting parties are involved, key management may create immense logistical problems and delays. Furthermore, in order to minimize the damage that could be caused by a compromised key, the keys may need to be short-lived and therefore frequently changed, adding to the logistical complexity. Public key cryptography can address many of the limitations of secret key cryptography regarding key management.
References[]
- ↑ Internet Security Glossary, at 295.
Source[]
- "Overview" section: Information Security: Advances and Remaining Challenges to Adoption of Public Key Infrastructure Technology, at 21-22.