Citation[]
National Security Council, The Comprehensive National Cybersecurity Initiative (CNCI) (May 2009) (full-text).
Overview[]
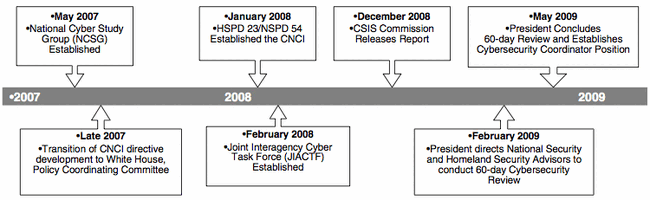
In January 2008, the Bush Administration established the CNCI by a classified joint presidential directive,[1] in an effort to make the United States more secure against cyber threats. The CNCI establishes a multi-pronged approach the federal government is to take in identifying current and emerging cyber threats, shoring up current and future telecommunications and cyber vulnerabilities, and responding to or proactively addressing entities that wish to steal or manipulate protected data on secure federal systems. The Homeland Security Presidential Directive 23 and National Security Presidential Directive 54 establishing the CNCI are still classified, although some details of the initiative have been made public through departmental press releases, speeches by executive branch leaders, and analysis offered by individuals who follow cybersecurity- and terrorism-related issues.
In a speech during his presidential campaign, President Obama promised to "make cyber security the top priority that it should be in the 21st century . . . and appoint a National Cyber Advisor who will report directly" to the President.[2] Shortly after taking office, President Obama, in February 2009, ordered a review of cybersecurity-related plans, programs, and activities underway throughout the federal government, including the CNCI projects. This review resulted in a May 2009 report that made recommendations for achieving a more reliable, resilient, and trustworthy digital infrastructure.
According to the Director of National Intelligence:
| “ | The CNCI addresses current cybersecurity threats, anticipates future threats and technologies, and develops a framework for creating in partnership with the private sector an environment that no longer favors cyber intruders over defenders. The CNCI includes defensive, offensive, education, research and development, and counterintelligence elements.[3] | ” |
Stated goals[]
The CNCI consists of a number of mutually reinforcing initiatives with the following major goals designed to help secure the United States in cyberspace:
- To establish a front line of defense against today’s immediate threats by creating or enhancing shared situational awareness of network vulnerabilities, threats, and events within the Federal Government — and ultimately with state, local, and tribal governments and private sector partners — and the ability to act quickly to reduce our current vulnerabilities and prevent intrusions.
- To defend against the full spectrum of threats by enhancing U.S. counterintelligence capabilities and increasing the security of the supply chain for key information technologies.
- To strengthen the future cybersecurity environment by expanding cyber education; coordinating and redirecting research and development efforts across the Federal Government; and working to define and develop strategies to deter hostile or malicious activity in cyberspace.
In building the plans for the CNCI, it was quickly realized that these goals could not be achieved without also strengthening certain key strategic foundational capabilities within the Government. Therefore, the CNCI includes funding within the federal law enforcement, intelligence, and defense communities to enhance such key functions as criminal investigation; intelligence collection, processing, and analysis; and information assurance critical to enabling national cybersecurity efforts.
The CNCI was developed with great care and attention to privacy and civil liberties concerns in close consultation with privacy experts across the government. Protecting civil liberties and privacy rights remain fundamental objectives in the implementation of the CNCI.
In accord with President Obama’s declared intent to make transparency a touchstone of his presidency, the Cyberspace Policy Review identified enhanced information sharing as a key component of effective cybersecurity. To improve public understanding of Federal efforts, the Cybersecurity Coordinator has directed the release of the following summary description of the CNCI.
Functions of the CNCI[]
Reportedly, the CNCI “establishes the policy, strategy, and guidelines to secure federal systems.”[4] The CNCI also delineates “an approach that anticipates future cyber threats and technologies, and requires the federal government to integrate many of its technical and organizational capabilities to better address sophisticated threats and vulnerabilities.”[5] Rather than serving as an overarching national strategy document with specific instructions for federal agency implementation activities, the CNCI is seen as a plan of action for programs and initiatives to be addressed at the operational and tactical level.
Given the classified nature of the presidential directives and the secrecy accompanying department and agency activities related to this issues, few details are known about CNCI-related federal government implementation efforts. According to one media account, Steven Chabinsky, Deputy Director of the Joint Interagency Cyber Task Force (JIACTF) for the Office of the Director of National Intelligence, stated at an information technology security conference that there are 12 objectives supporting the initiative’s goal of comprehensively addressing the nation’s cyber security concerns.[6] These include the following:
- Move toward managing a single federal enterprise network (an integrated communications system architecture for the federal government with common security standards across the network).
- Deploy intrinsic detection systems.
- Develop and deploy intrusion prevention tools.
- Review and potentially redirect research and funding.
- Connect current government cyber operations centers.
- Develop a government-wide cyber intelligence plan.
- Increase the security of classified networks.
- Expand cyber education.
- Define enduring leap-ahead technologies (investing in high-risk, high-reward research and development to ensure transformational change).
- Define enduring deterrent technologies and programs.
- Develop multi-pronged approaches to supply chain risk management (potential tampering within the production line and the risk associated with computer products and parts made outside the United States).
- Define the role of cybersecurity in private sector domains.[7]
Ongoing projects[]
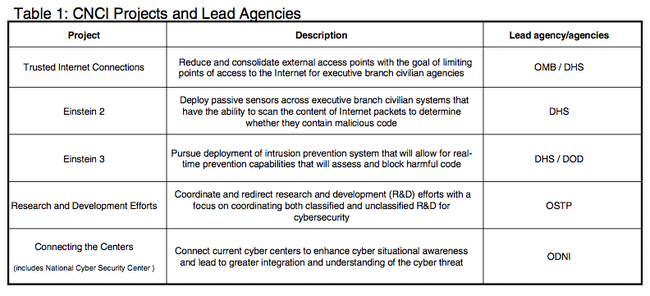
While The NSPD-54/HSPD-23) are classified, the Obama Administration released a description of them in March 2010.[8] NSPD-54/HSPD-23 established 12 CNCI projects and identified lead agencies for each. Since January 2008, the lead agencies have been responsible for tracking progress on each of the projects specified in the directive.
Four agencies have responsibilities for multiple projects of CNCI:
- Department of Homeland Security's responsibilities focus on protecting civilian agency information systems, including reducing and consolidating external access points, deploying passive network sensors, and defining public and private partnerships.
- The Department of Defense is charged with monitoring military information systems, increasing the security of classified networks, and deploying intrusion prevention systems, among other things.
- The Office of the Director of National Intelligence (ODNI) is responsible for monitoring intelligence community information systems and other intelligence-related activities, including the development of a government-wide cyber counterintelligence plan.
- The Office of Science and Technology Policy (OSTP), which is responsible for providing advice on the effects of science and technology on domestic and international affairs, is responsible for the two CNCI projects that focus on advanced technology research and development.
The Office of Management and Budget, the Department of Justice, and the National Security Council also have lead roles on specific CNCI projects.
The twelve projects currently being pursued under the CNCI are:
Criticism of the CNCI[]
In response to the CNCI and other proposals, questions have emerged regarding: (1) the adequacy of existing legal authorities — statutory or constitutional — for responding to cyber threats; and (2) the appropriate roles for the executive and legislative branches in addressing cybersecurity. The new and emerging nature of cyber threats complicates these questions. Although existing statutory provisions might authorize some modest actions, inherent constitutional powers currently provide the most plausible legal basis for many potential executive responses to national, security-related cyber incidences.
Given that cyber threats originate from various sources, it is difficult to determine whether actions to prevent cyberattacks fit within the traditional scope of executive power to conduct war and foreign affairs. Nonetheless, under the Supreme Court jurisprudence, it appears that the President is not prevented from taking action in the cybersecurity arena, at least until Congress takes further action. Regardless, Congress has a continuing oversight and appropriations role. In addition, potential government responses could be limited by individuals’ constitutional rights or international laws of war.
Lack of transparency[]
Since CNCI’s inception, former and current government officials have voiced concerns regarding the lack of publicly available information. For example:
- The federally-chartered Information Security and Privacy Advisory Board (ISPAB) stated that greater clarity and transparency was necessary to ensure both the effectiveness and trustworthiness of CNCI. Specifically, the ISPAB advised that government agencies release key documentation regarding the impact of CNCI activities on personal privacy.
- The CSIS commission noted that because the CNCI directive and projects are classified, little information could be shared with the public, the cybersecurity industry, or allied nations. The commission concluded that greater openness is important given the large role played by those outside the federal government in cybersecurity. In addition, the commission stated that the United States should open the discussion of how best to secure cyberspace and present the issues of deterrence and national strategy to the broad national community of experts and stakeholders.
- The White House policy review stated that, in moving forward, transparency would be important to build trust between the public and federal cybersecurity programs. The review added that it would be important to bring transparency and effective management to the overall cybersecurity portfolio.
While certain aspects and details of CNCI must necessarily remain classified, it is claimed that the lack of transparency regarding CNCI projects hinders accountability to Congress and the public. In addition, current classification may make it difficult for some agencies, as well as the private sector, to interact and contribute to the success of CNCI projects.
Interagency cybersecurity review[]
On February 9, 2009, President Obama directed a 60-day interagency cybersecurity review (Cyberspace Policy Review) to develop a strategic framework to ensure the CNCI is being appropriately integrated, resourced, and coordinated with Congress and the private sector.[9] On May 29, 2009, President Obama issued the results of the Administration’s 60-Day Cyberspace Policy Review.
Obama administration initiatives[]
The Cybersecurity Coordinator has released of the following summary description of current CNCI initiatives.
Initiative #1. Manage the Federal Enterprise Network as a single network enterprise with Trusted Internet Connections[]
The Trusted Internet Connections (TIC) initiative, headed by the Office of Management and Budget and the Department of Homeland Security, covers the consolidation of the Federal Government's external access points (including those to the Internet). This consolidation will result in a common security solution which includes: facilitating the reduction of external access points, establishing baseline security capabilities; and, validating agency adherence to those security capabilities. Agencies participate in the TIC initiative either as TIC Access Providers (a limited number of agencies that operate their own capabilities) or by contracting with commercial Managed Trusted Internet Protocol Service (MTIPS) providers through the GSA-managed NETWORX contract vehicle.
Initiative #2. Deploy an intrusion detection system of sensors across the Federal enterprise[]
Intrusion Detection Systems using passive sensors form a vital part of U.S. Government network defenses by identifying when unauthorized users attempt to gain access to those networks. The Department of Homeland Security (DHS) is deploying, as part of its EINSTEIN 2 activities, signature-based sensors capable of inspecting Internet traffic entering Federal systems for unauthorized accesses and malicious content. The EINSTEIN 2 capability enables analysis of network flow information to identify potential malicious activity while conducting automatic full packet inspection of traffic entering or exiting U.S. Government networks for malicious activity using signature-based intrusion detection technology.
Associated with this investment in technology is a parallel investment in manpower with the expertise required to accomplish DHS's expanded network security mission. EINSTEIN 2 is capable of alerting US-CERT in real time to the presence of malicious or potentially harmful activity in federal network traffic and provides correlation and visualization of the derived data. Due to the capabilities within EINSTEIN 2, US-CERT analysts have a greatly improved understanding of the network environment and an increased ability to address the weaknesses and vulnerabilities in Federal network security. As a result, US-CERT has greater situational awareness and can more effectively develop and more readily share security-relevant information with network defenders across the U.S. Government, as well as with security professionals in the private sector and the American public.
The Department of Homeland Security's Privacy Office has conducted and published a Privacy Impact Assessment for the EINSTEIN 2 program — Privacy Compliance Review of the EINSTEIN Program.
Initiative #3. Pursue deployment of intrusion prevention systems across the Federal enterprise.[]
This Initiative represents the next evolution of protection for civilian Departments and Agencies of the Federal Executive Branch. This approach, called EINSTEIN 3, will draw on commercial technology and specialized government technology to conduct real-time full packet inspection and threat-based decision-making on network traffic entering or leaving these Executive Branch networks. The goal of EINSTEIN 3 is to identify and characterize malicious network traffic to enhance cybersecurity analysis, situational awareness and security response. It will have the ability to automatically detect and respond appropriately to cyber threats before harm is done, providing an intrusion prevention system supporting dynamic defense.
EINSTEIN 3 will assist DHS US-CERT in defending, protecting and reducing vulnerabilities on Federal Executive Branch networks and systems. The EINSTEIN 3 system will also support enhanced information sharing by US-CERT with Federal Departments and Agencies by giving DHS the ability to automate alerting of detected network intrusion attempts and, when deemed necessary by DHS, to send alerts that do not contain the content of communications to the National Security Agency (NSA) so that DHS efforts may be supported by NSA exercising its lawfully authorized missions. This initiative makes substantial and long-term investments to increase national intelligence capabilities to discover critical information about foreign cyber threats and use this insight to inform EINSTEIN 3 systems in real time. DHS will be able to adapt threat signatures determined by NSA in the course of its foreign intelligence and DoD information assurance missions for use in the EINSTEIN 3 system in support of DHS's federal system security mission. Information sharing on cyber intrusions will be conducted in accordance with the laws and oversight for activities related to homeland security, intelligence, and defense in order to protect the privacy and rights of U.S. citizens.
DHS is currently conducting a exercise to pilot the EINSTEIN 3 capabilities described in this initiative based on technology developed by NSA and to solidify processes for managing and protecting information gleaned from observed cyber intrusions against civilian Executive Branch systems. Government civil liberties and privacy officials are working closely with DHS and US-CERT to build appropriate and necessary privacy protections into the design and operational deployment of EINSTEIN 3.
Initiative #4: Coordinate and redirect research and development (R&D) efforts[]
No single individual or organization is aware of all of the cyber-related R&D activities being funded by the Government. This initiative is developing strategies and structures for coordinating all cyber R&D sponsored or conducted by the U.S. government, both classified and unclassified, and to redirect that R&D where needed. This Initiative is critical to eliminate redundancies in federally funded cybersecurity research, and to identify research gaps, prioritize R&D efforts, and ensure the taxpayers are getting full value for their money as we shape our strategic investments.
Initiative #5. Connect current cyber ops centers to enhance situational awareness[]
There is a pressing need to ensure that government information security offices and strategic operations centers share data regarding malicious activities against federal systems, consistent with privacy protections for personally identifiable and other protected information and as legally appropriate, in order to have a better understanding of the entire threat to government systems and to take maximum advantage of each organization's unique capabilities to produce the best overall national cyber defense possible. This initiative provides the key means necessary to enable and support shared situational awareness and collaboration across six centers that are responsible for carrying out U.S. cyber activities. This effort focuses on key aspects necessary to enable practical mission bridging across the elements of U.S. cyber activities: foundational capabilities and investments such as upgraded infrastructure, increased bandwidth, and integrated operational capabilities; enhanced collaboration, including common technology, tools, and procedures; and enhanced shared situational awareness through shared analytic and collaborative technologies.
The National Cyber Security Center (NCSC) within the Department of Homeland Security will play a key role in securing U.S. Government networks and systems under this initiative by coordinating and integrating information from the six centers to provide cross-domain situational awareness, analyzing and reporting on the state of U.S. networks and systems, and fostering interagency collaboration and coordination.
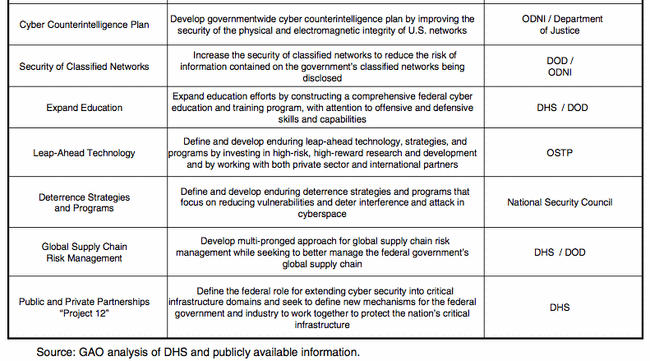
Initiative #6. Develop and implement a government-wide cyber counterintelligence (CI) plan[]
A government-wide cyber counterintelligence plan is necessary to coordinate activities across all Federal Agencies to detect, deter, and mitigate the foreign-sponsored cyber intelligence threat to U.S. and private sector information systems. To accomplish these goals, the plan establishes and expands cyber CI education and awareness programs and workforce development to integrate CI into all cyber operations and cyber analysis, increase employee awareness of the cyber CI threat, and increase counterintelligence collaboration across the government. The Cyber CI Plan is aligned with the National Counterintelligence Strategy of the United States of America (2007) and supports the other programmatic elements of the CNCI.
Initiative #7. Increase the security of our classified networks[]
Classified networks house the Federal Government's most sensitive information and enable crucial war-fighting, diplomatic, counterterrorism, law enforcement, intelligence, and homeland security operations. Successful penetration or disruption of these networks could cause exceptionally grave damage to national security. The government needs to exercise due diligence in ensuring the integrity of these networks and the data they contain.
Initiative #8. Expand cyber education[]
While billions of dollars are being spent on new technologies to secure the U.S. Government in cyberspace, it is the people with the right knowledge, skills, and abilities to implement those technologies who will determine success. However there are not enough cybersecurity experts within the Federal Government or private sector to implement the CNCI, nor is there an adequately established Federal cybersecurity career field. Existing cybersecurity training and personnel development programs, while good, are limited in focus and lack unity of effort. In order to effectively ensure our continued technical advantage and future cybersecurity, we must develop a technologically-skilled and cyber-savvy workforce and an effective pipeline of future employees. It will take a national strategy, similar to the effort to upgrade science and mathematics education in the 1950s, to meet this challenge.
Initiative #9. Define and develop enduring "leap-ahead" technology, strategies, and programs[]
One goal of the CNCI is to develop technologies that provide increases in cybersecurity by orders of magnitude above current systems and which can be deployed within 5 to 10 years. This initiative seeks to develop strategies and programs to enhance the component of the government R&D portfolio that pursues high-risk/high-payoff solutions to critical cybersecurity problems. The Federal Government has begun to outline Grand Challenges for the research community to help solve these difficult problems that require "out of the box" thinking. In dealing with the private sector, the government is identifying and communicating common needs that should drive mutual investment in key research areas.
Initiative #10. Define and develop enduring deterrence strategies and programs[]
U.S. senior policymakers must think through the long-range strategic options available to the United States in a world that depends on assuring the use of cyberspace. To date, the U.S. Government has been implementing traditional approaches to the cybersecurity problem — and these measures have not achieved the level of security needed. This Initiative is aimed at building an approach to cyber defense strategy that deters interference and attack in cyberspace by improving warning capabilities, articulating roles for private sector and international partners, and developing appropriate responses for both state and non-state actors.
Initiative #11. Develop a multi-pronged approach for global supply chain risk management[]
Globalization of the commercial information and communications technology marketplace provides increased opportunities for those intent on harming the United States by penetrating the supply chain to gain unauthorized access to data, alter data, or interrupt communications. Risks stemming from both the domestic and globalized supply chain must be managed in a strategic and comprehensive way over the entire lifecycle of products, systems and services. Managing this risk will require a greater awareness of the threats, vulnerabilities, and consequences associated with acquisition decisions; the development and employment of tools and resources to technically and operationally mitigate risk across the lifecycle of products (from design through retirement); the development of new acquisition [[policies] and practices that reflect the complex global marketplace; and partnership with industry to develop and adopt supply chain and risk management standards and best practices. This initiative will enhance Federal Government skills, policies, and processes to provide departments and agencies with a robust toolset to better manage and mitigate supply chain risk at levels commensurate with the criticality of, and risks to, their systems and networks.
Initiative #12. Define the Federal role for extending cybersecurity into critical infrastructure domains[]
The U.S. Government depends on a variety of privately owned and operated critical infrastructures to carry out the public's business. In turn, these critical infrastructures rely on the efficient operation of information systems and networks that are vulnerable to malicious cyber threats. This Initiative builds on the existing and ongoing partnership between the Federal Government and the public and private sector owners and operators of critical infrastructure and key resources (CIKR).
The Department of Homeland Security and its private-sector partners have developed a plan of shared action with an aggressive series of milestones and activities. It includes both short-term and long-term recommendations, specifically incorporating and leveraging previous accomplishments and activities that are already underway. It addresses security and information assurance efforts across the cyber infrastructure to increase resiliency and operational capabilities throughout the CIKR sectors. It includes a focus on public-private sharing of information regarding cyber threats and incidents in both government and CIKR.
References[]
- ↑ White House, National Security Presidential Directive 54/Homeland Security Presidential Directive 23 (NSPD-54/HSPD-23) (Jan. 8, 2008).
- ↑ July 17, 2008 speech at Purdue University.
- ↑ Dennis Blair, Director of National Intelligence, Annual Threat Assessment of the Intelligence Community for the Senate Select Committee on Intelligence (Feb. 12, 2009) (full-text).
- ↑ Department of Homeland Security, "Fact Sheet: DHS End-of-Year Accomplishments" (Dec. 18, 2008).[1]
- ↑ Department of Homeland Security, "Department Responsibilities: Maximize Use of Science, Technology and Innovation."[2]
- ↑ Jill R. Aitoro, “National Cyber Security Initiative will have a dozen parts,” NextGov (Aug. 1, 2008).
- ↑ Wyatt Kash, "Details Merge About the President’s Cyber Plan," Government Computer News (Nov. 21, 2008).[3]
- ↑ The White House, The Comprehensive National Cybersecurity Initiative (Mar. 5, 2010) (full-text).
- ↑ The White House, Office of the Press Secretary, "President Obama Directs the National Security and Homeland Security Advisors to Conduct Immediate Cyber Security Review" (Feb. 9, 2009).[4]
Sources[]
- Comprehensive National Cybersecurity Initiative: Legal Authorities and Policy Considerations.
- The Comprehensive National Cybersecurity Initiative.
See also[]
- Cybersecurity: Progress Made but Challenges Remain in Defining and Coordinating the Comprehensive National Initiative.
- Office of the Director of National Intelligence, Comprehensive National Security Initiative: Goals, Plans, and Performance Measures (Mar. 2008).